How to debug communication between your server and Apple APNS
I had a problem with my Server (IBM Traveler) to send push messages with Apple Push Notification Service (APNS). And not found a good information about how to check communication with APNS. In this article, i share how to debug using Tcpdump and Wireshark.
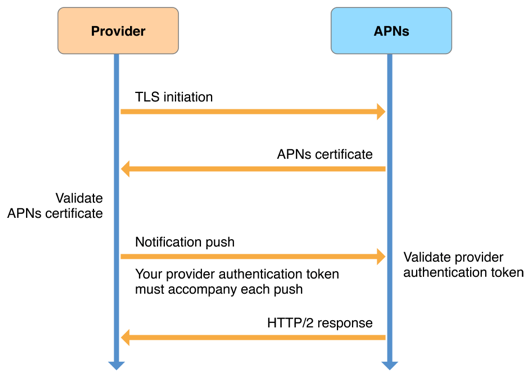
How communication between You Server/Traveler and Apple APNS works?
You can get details here.
If have problems between your Server/IBM Traveler and Apple APNS, you can use tcpdump and wireshark to debug traffic between these 2 services.
How can i found this information on Wireshark?
First you need to collect be using tcpdump
tcpdump -w myserver_apple_capture.pcap -i any -ePnn -s 1500 host 192.168.253.103 and port 2195
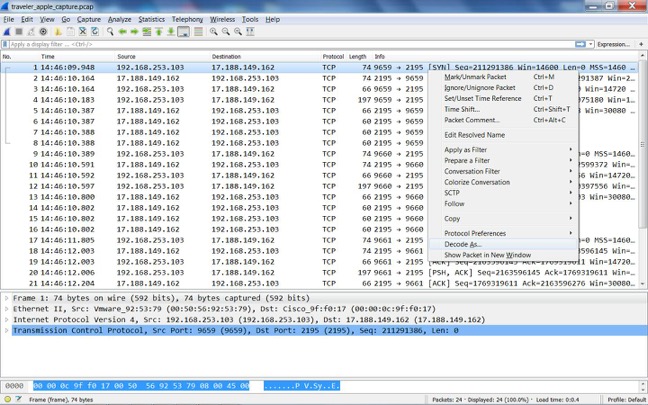
After collect data open this file in Wireshark.
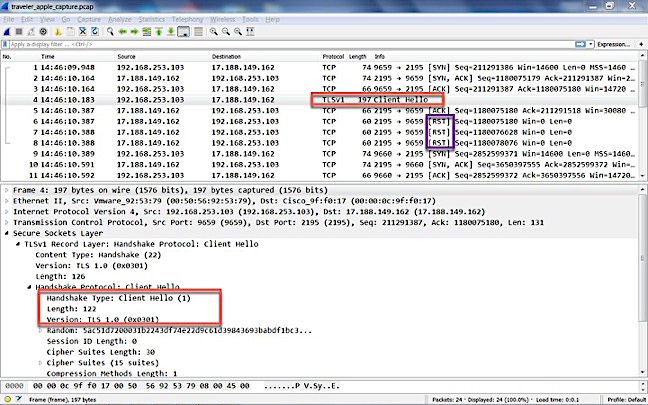
Traveler is communicating with Apple on tcp/2195, so find a packet going to tcp/2195 at Apple's IP address, right-click on it, and select "Decode As", like this:
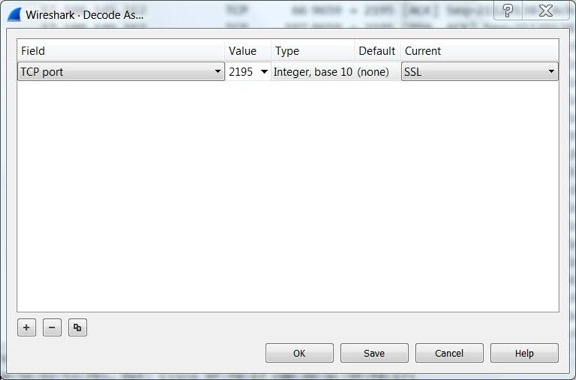
Then, in the dialog box, tell Wireshark to decode port 2195 as SSL, like this:
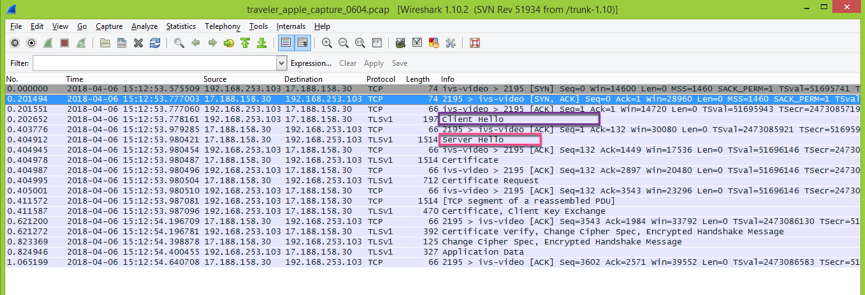
When you hit OK, you'll see that Wireshark now identifies SSL/TLS. In this image you can see Client Hello and a Server Hello, that means the TLS handshake, between Traveler and Apple Push.
In this example, my server is connecting to Apple, but NOT receives a Server Hello (TLS Handshake) from Apple. So, push cannot be sent to iOS devices.
How can i found this information on Tcpdump?
If you have experience with tcpdump, you can see this example useful:
Example of command to check a correct communication between Traveler and Apple APNS.
tcpdump -i any -ePnn -s 1500 host 192.168.253.103 and port 2195
Result:
11:14:55.854401 eth3-02.21[in ]: 192.168.253.103.61983 > 17.188.134.26.2195: S 1367157684:1367157684(0) win 14600 <mss 1460,sackOK,timestamp 48272772 0,nop,wscale 7> 11:14:55.855457 eth1-07[out]: 192.168.253.103.61983 > 17.188.134.26.2195: S 1367157684:1367157684(0) win 14600 <mss 1460,sackOK,timestamp 48272772 0,nop,wscale 7> 11:14:56.044988 eth3-02.21[out]: 17.188.134.26.2195 > 192.168.253.103.61983: S 2807876383:2807876383(0) ack 1367157685 win 28960 <mss 1460,sackOK,timestamp 460176732 48272772,nop,wscale 7> 11:14:56.044992 eth3-02[out]: 17.188.134.26.2195 > 192.168.253.103.61983: S 2807876383:2807876383(0) ack 1367157685 win 28960 <mss 1460,sackOK,timestamp 460176732 48272772,nop,wscale 7> 11:14:56.061795 eth3-02.21[in ]: 170.66.1.140.12970 > 17.188.134.26.2195: . ack 2807876384 win 115 <nop,nop,timestamp 48272963 460176732> 11:14:56.061816 eth3-02.21[in ]: 170.66.1.140.12970 > 17.188.134.26.2195: P 0:131(131) ack 1 win 115 <nop,nop,timestamp 48272964 460176732> 11:14:56.251950 eth3-02.21[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . ack 132 win 235 <nop,nop,timestamp 460176938 48272964> 11:14:56.251953 eth3-02[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . ack 132 win 235 <nop,nop,timestamp 460176938 48272964> 11:14:56.253137 eth3-02.21[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . 1:1449(1448) ack 132 win 235 <nop,nop,timestamp 460176939 48272964> 11:14:56.253140 eth3-02[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . 1:1449(1448) ack 132 win 235 <nop,nop,timestamp 460176939 48272964> 11:14:56.253230 eth3-02.21[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . 1449:2897(1448) ack 132 win 235 <nop,nop,timestamp 460176939 48272964> 11:14:56.253232 eth3-02[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . 1449:2897(1448) ack 132 win 235 <nop,nop,timestamp 460176939 48272964> 11:14:56.253278 eth3-02.21[out]: 17.188.134.26.2195 > 192.168.253.103.61983: P 2897:3543(646) ack 132 win 235 <nop,nop,timestamp 460176939 48272964> 11:14:56.253279 eth3-02[out]: 17.188.134.26.2195 > 192.168.253.103.61983: P 2897:3543(646) ack 132 win 235 <nop,nop,timestamp 460176939 48272964> 11:14:56.253564 eth3-02.21[in ]: 170.66.1.140.12970 > 17.188.134.26.2195: . ack 1449 win 137 <nop,nop,timestamp 48273171 460176939> 11:14:56.253641 eth3-02.21[in ]: 170.66.1.140.12970 > 17.188.134.26.2195: . ack 3543 win 160 <nop,nop,timestamp 48273171 460176939> 11:14:56.269128 eth3-02.21[in ]: 192.168.253.103.61983 > 17.188.134.26.2195: . 132:1580(1448) ack 3543 win 160 <nop,nop,timestamp 48273186 460176939> 11:14:56.269133 eth3-02.21[in ]: 192.168.253.103.61983 > 17.188.134.26.2195: P 1580:1984(404) ack 3543 win 160 <nop,nop,timestamp 48273186 460176939> 11:14:56.459549 eth3-02.21[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . ack 1984 win 280 <nop,nop,timestamp 460177146 48273186> 11:14:56.459552 eth3-02[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . ack 1984 win 280 <nop,nop,timestamp 460177146 48273186> 11:14:56.459995 eth3-02.21[in ]: 170.66.1.140.12970 > 17.188.134.26.2195: P 1983:2309(326) ack 3543 win 160 <nop,nop,timestamp 48273377 460177146> 11:14:56.651364 eth3-02.21[out]: 17.188.134.26.2195 > 192.168.253.103.61983: P 3543:3602(59) ack 2310 win 303 <nop,nop,timestamp 460177338 48273377> 11:14:56.651368 eth3-02[out]: 17.188.134.26.2195 > 192.168.253.103.61983: P 3543:3602(59) ack 2310 win 303 <nop,nop,timestamp 460177338 48273377> 11:14:56.652869 eth3-02.21[in ]: 192.168.253.103.61983 > 17.188.134.26.2195: P 2310:2635(325) ack 3602 win 160 <nop,nop,timestamp 48273570 460177338> 11:14:56.884952 eth3-02.21[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . ack 2635 win 326 <nop,nop,timestamp 460177570 48273570> 11:14:56.884956 eth3-02[out]: 17.188.134.26.2195 > 192.168.253.103.61983: . ack 2635 win 326 <nop,nop,timestamp 460177570 48273570> 77 packets captured 309 packets received by filter 17 packets dropped by kernel
How to test communication using openssl?
Maybe can be a problem with TLS Certificates, you use this technote: